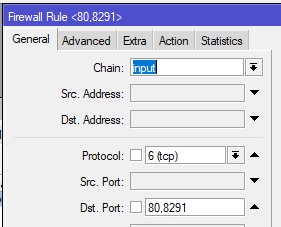
FPC-8291 Two Doors Professional Access Control Electric Drop Bolt Fail Secure TCP / IP Wiegand Controller Box, Outdoor Keypad / Reader, Software Included, Receiver, PIR, 20,000 Users, 70,000 Records - FPC Security

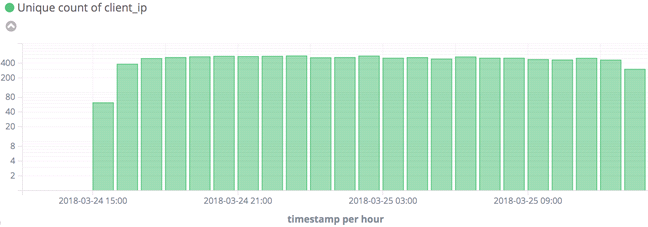
Ground truth list of TCP ports used for cyberthreats observed on our... | Download Scientific Diagram

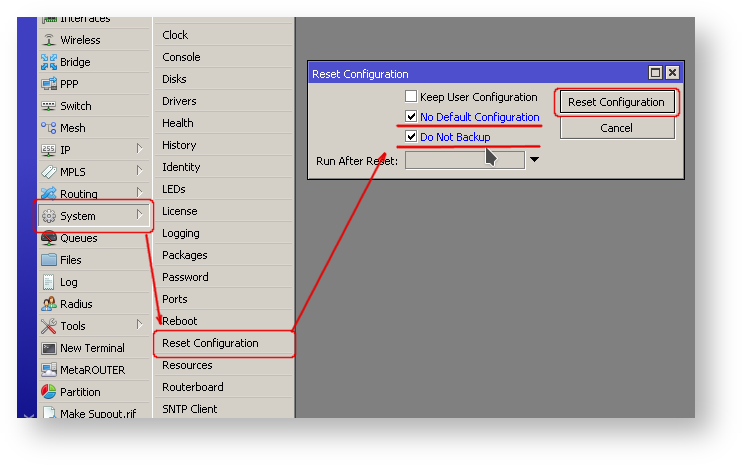
Uncovering Trickbot's use of IoT devices in command-and-control infrastructure - Microsoft Security Blog