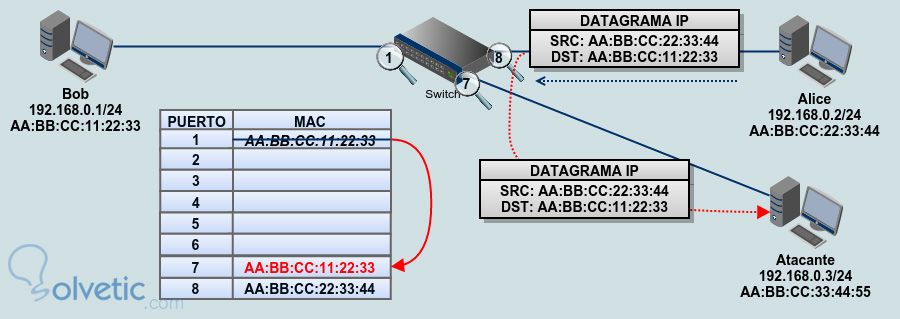
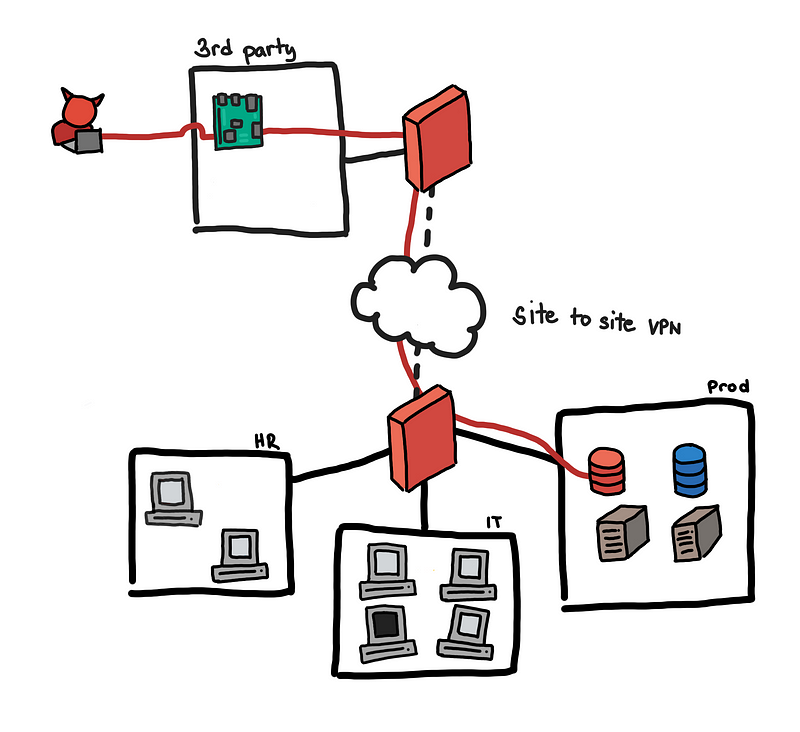
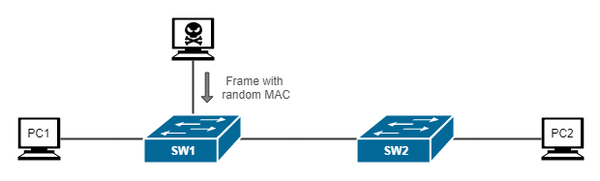
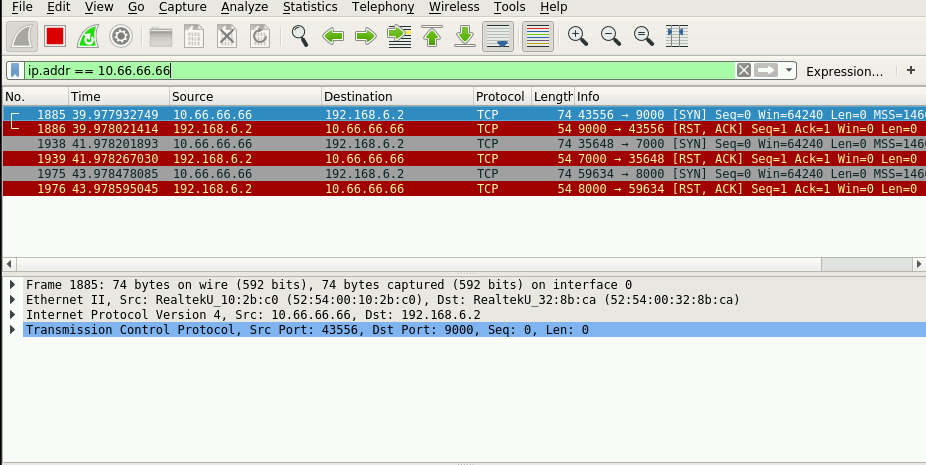
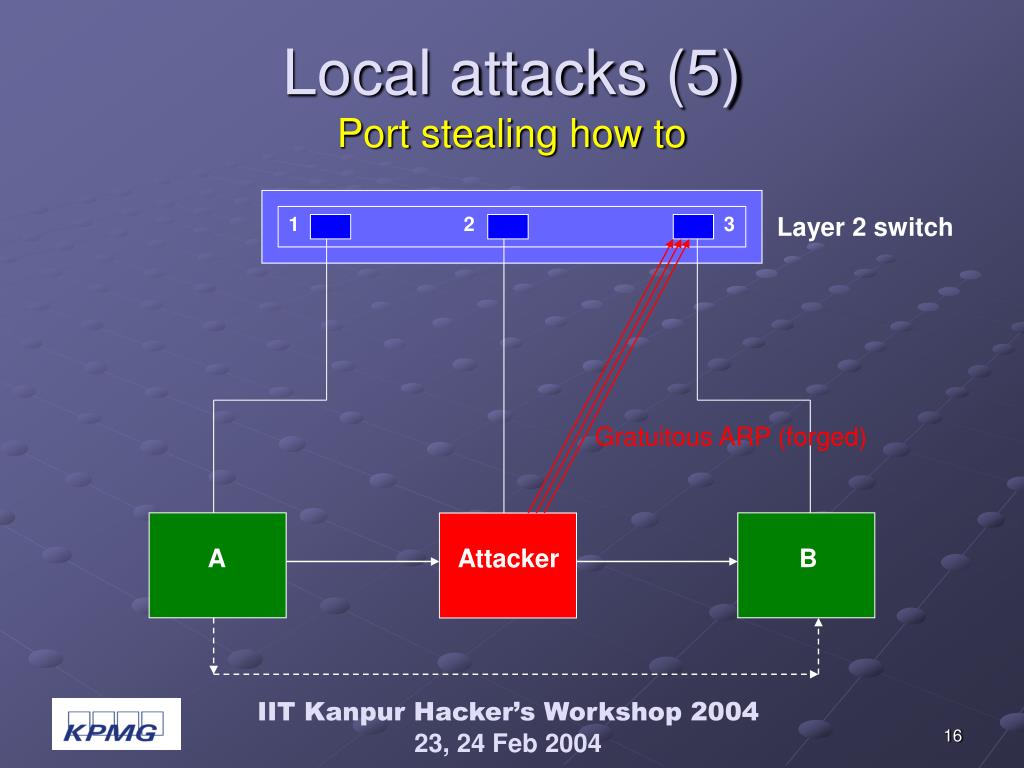
Threats Behind Default Configurations of Network Devices: Wired Local Network Attacks and Their Countermeasures | SpringerLink

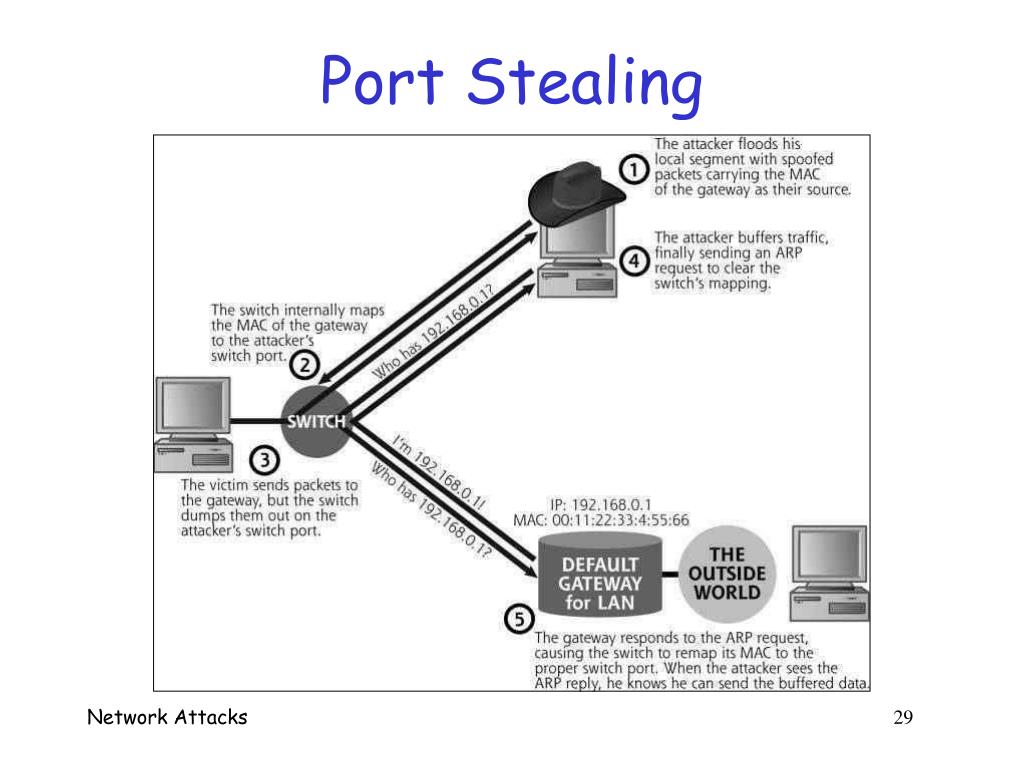
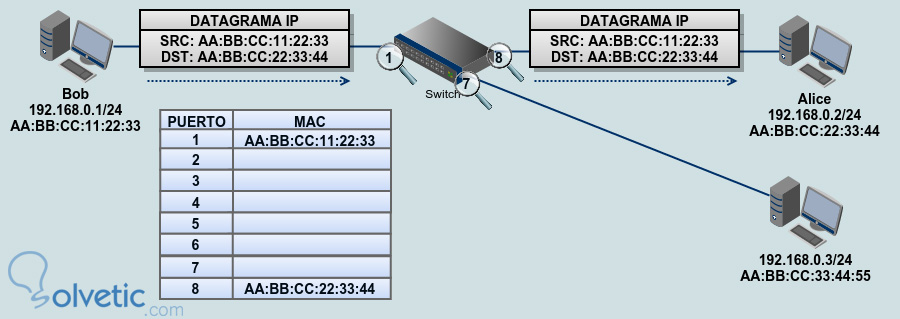
The attacker performs a port stealing attack targeting the PLC via the... | Download Scientific Diagram

The attacker performs a port stealing attack targeting the PLC via the... | Download Scientific Diagram



![PDF] Packet Sniffing on Layer 2 Switched Local Area Networks | Semantic Scholar PDF] Packet Sniffing on Layer 2 Switched Local Area Networks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/86d1954c619c72017b458cd09041e47eb29f6c14/5-Figure2-1.png)