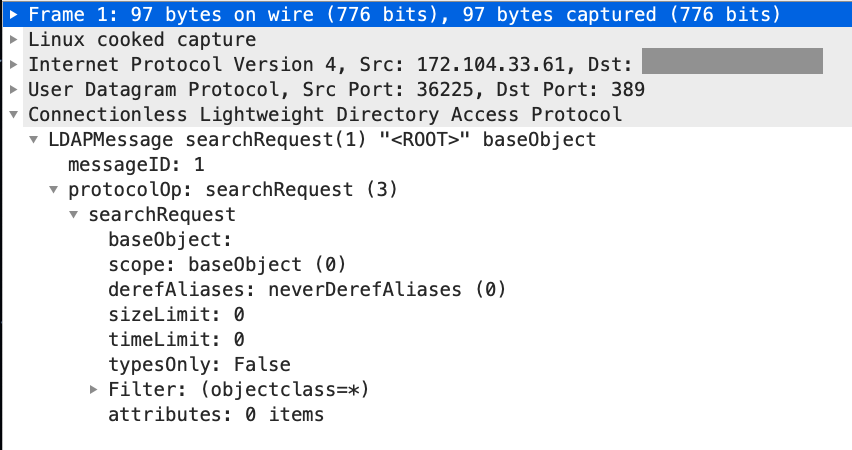
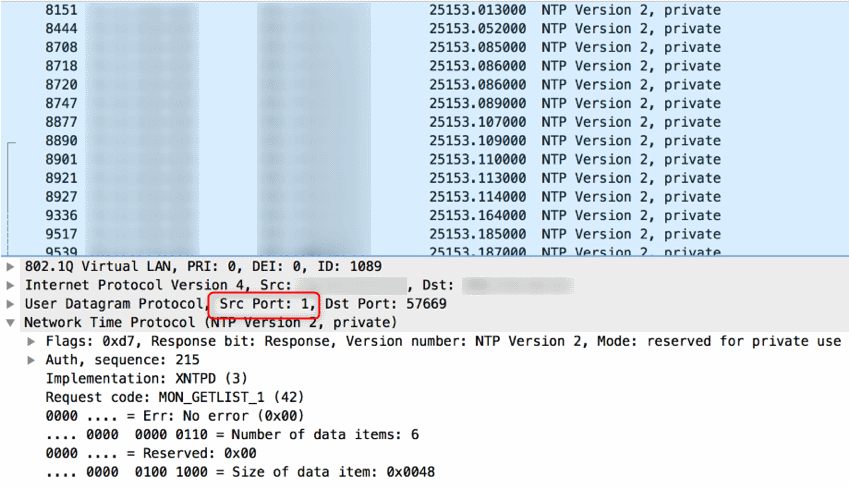
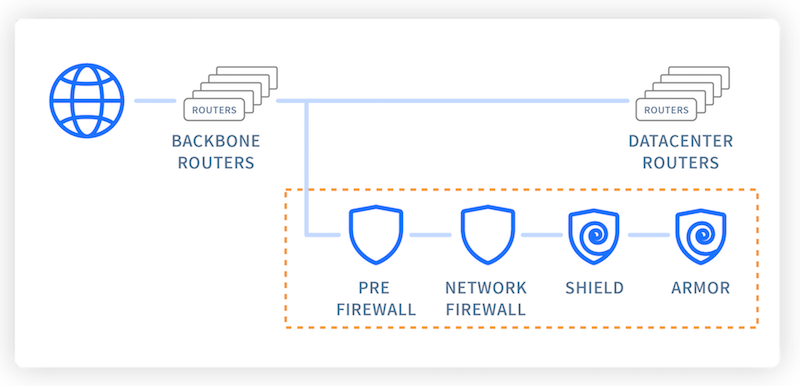
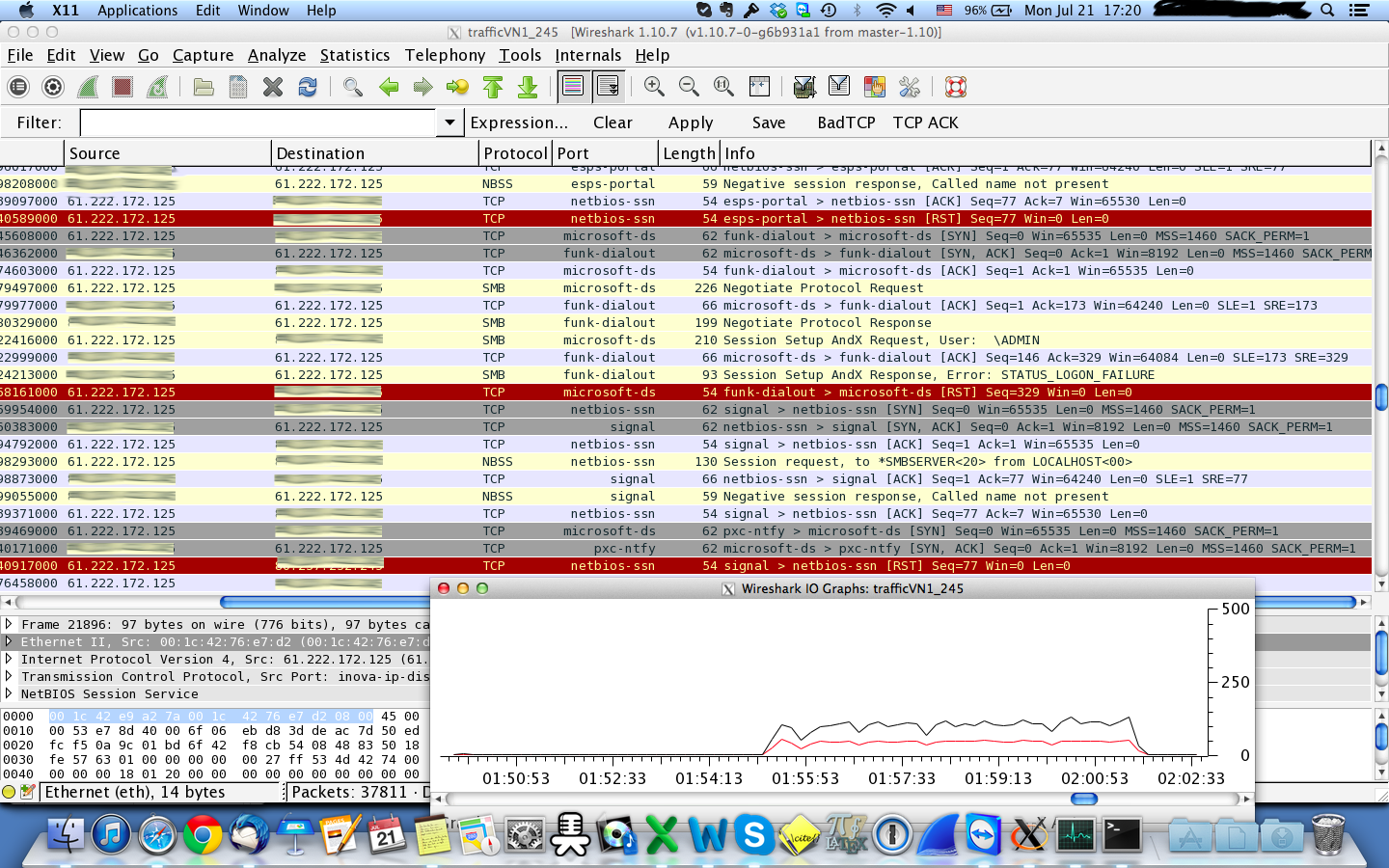
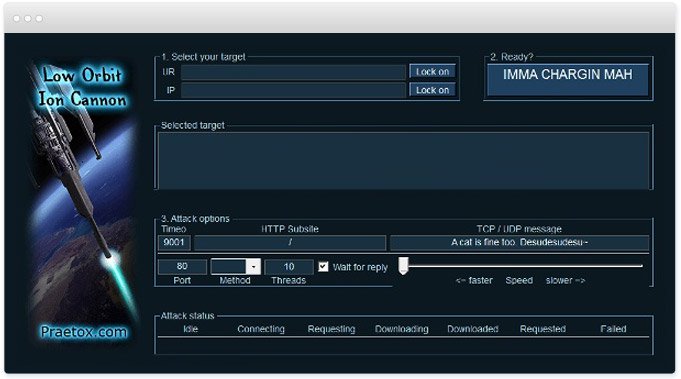
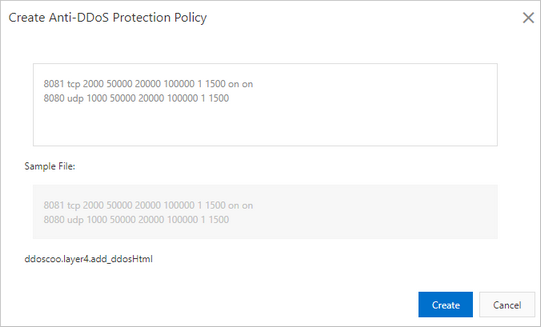
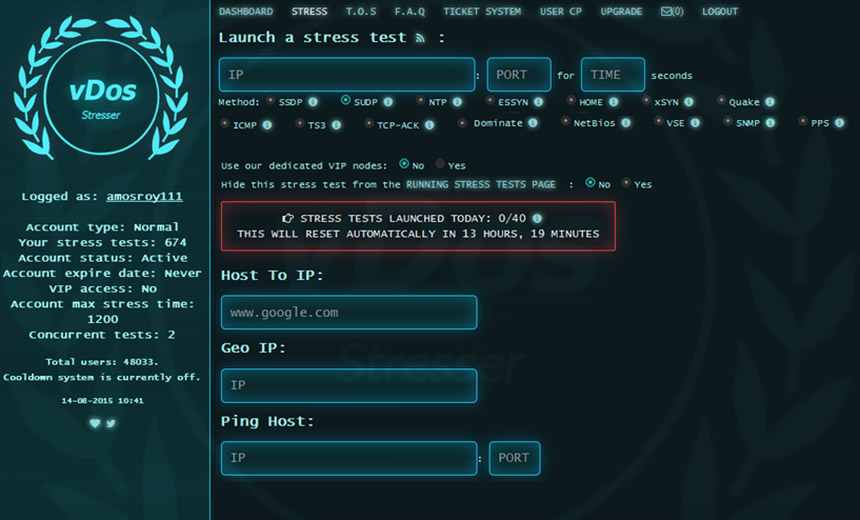
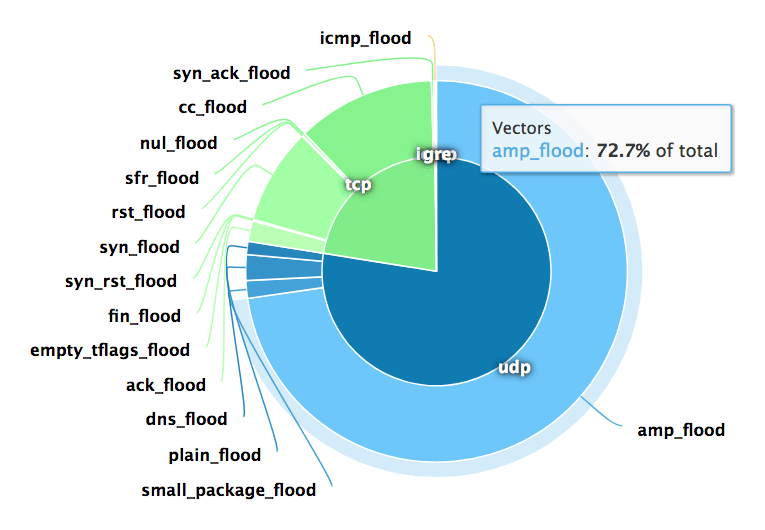
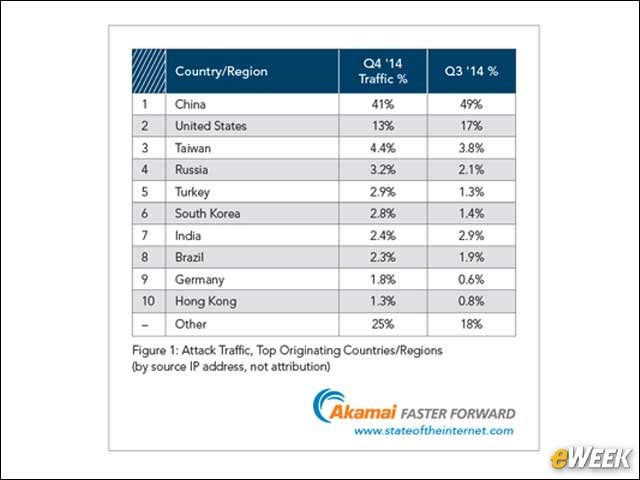
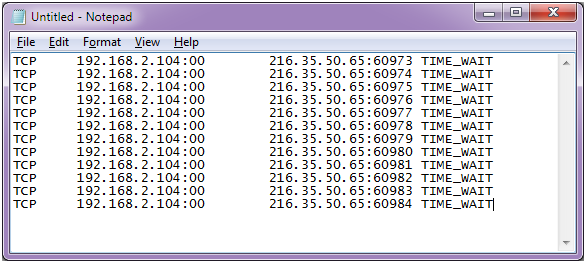
udp flood port 53 Blues!!! (PFsense and DDos Help) "not Dos, if it was just 1 or even 50 ip's I could do it, I have 1000's" | Overclock.net
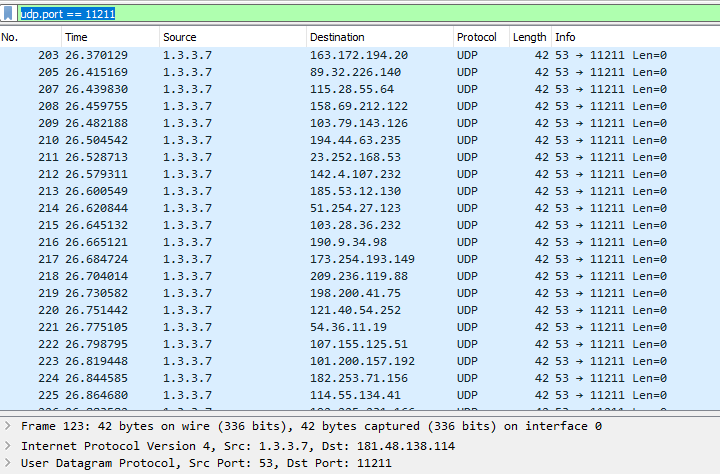
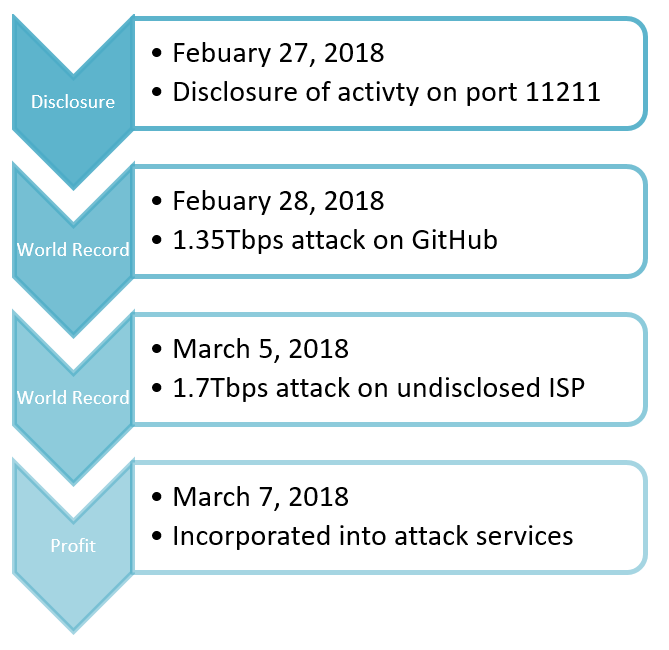
GitHub - 649/Memcrashed-DDoS-Exploit: DDoS attack tool for sending forged UDP packets to vulnerable Memcached servers obtained using Shodan API